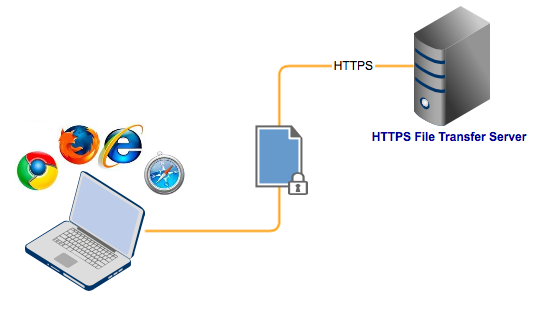
How To Set Up A HTTPS File Transfer: HTTPS File Sharing
To set up a web-based HTTPS file transfer, launch JSCAPE MFT Server Manager, go to Settings > Web, enable both HTTP and HTTPS on your host, and redirect HTTP requests to HTTPS for secure access. Next, activate HTTPS service on your desired domain, prepare server keys for encryption, and select SSL/TLS cipher suites for secure data exchange. This process ensures secure HTTPS file sharing with advanced settings for enhanced security and compatibility.
Overview
In this post, you'll learn how to set up a HTTPS file transfer. We'll begin with a Quick Start, where you'll use the default settings in order to get a HTTPS file transfer service up and running with just a few clicks. After that, we'll tackle some of the more advanced settings so you can choose your desired set of SSL/TLS cipher suites and server key. Your choice of cipher suites and keys will have an effect on the security of your HTTPS file sharing and its compatibility with your users' web browsers.
Note: The HTTPS or HTTP Secure protocol is defined in RFC 2818, so if you want a technical discussion on HTTPS read that.
Note: JSCAPE's HTTPS is not affected by the Heartbleed vulnerability
Prefer To Watch A Video Of This Tutorial Instead?
Getting Started
Let's proceed with the Quick Start.
1. Enable HTTPS On Your Host
Launch your JSCAPE MFT Server Manager and go to the Settings menu
Next, go to the Web module. In the Web tab, tick both the HTTP on host and HTTPS on host checkboxes. Why do we have to tick the HTTP on the host checkbox, too? Because if we leave that unchecked, end users who attempt to connect via HTTP (which is usually the default action on most browsers) will get an "Unable to connect" error.
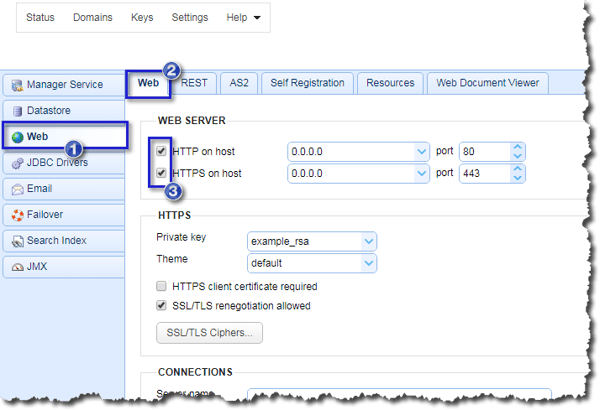
Of course, since we want our users to connect to the secure HTTPS file-sharing service (and not the unencrypted HTTP service), we have to ensure they are redirected to the HTTPS service even if they initially attempt to connect via HTTP. To do that, scroll down to the Connections panel and then tick the checkbox labeled Redirect HTTP requests to HTTPS.
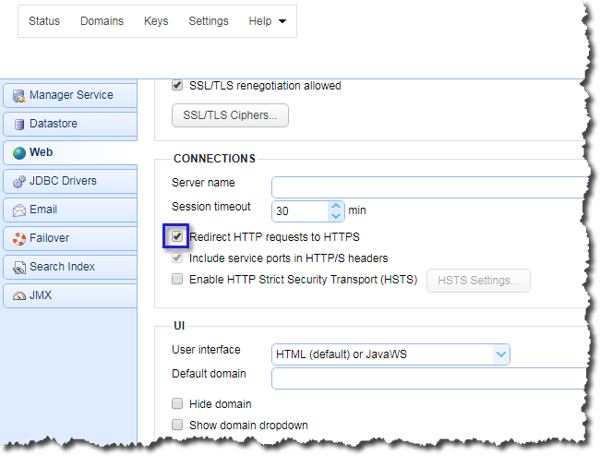
The settings we made will allow end users to enter your server's hostname or IP address as normal (usually via HTTP) and then redirect them to your HTTPS connection without them noticing.
So, for example, if a user enters either of the following into their browser:
https://domain.com
or
domain.com - in which case most browsers would automatically append https:// to the beginning.
JSCAPE MFT Server will automatically redirect the browser to your HTTPS service.
When you're done, click the Apply button to the bottom-right corner of that page.
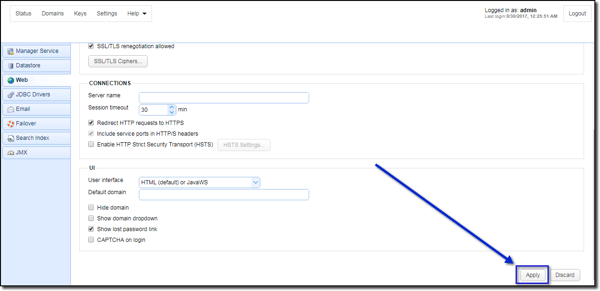
Note: If you just configure the server up to this point, your end users will be able to connect to it and see the login screen. They'll even be able to enter values into the fields, but that's about it. They won't be able to login to the server. That's why you need to proceed to step 2.
2. Activate The HTTPS Service On Your Desired Domain
Go to the Domains tab, select the domain where you want HTTPS activated, and click the Edit button.
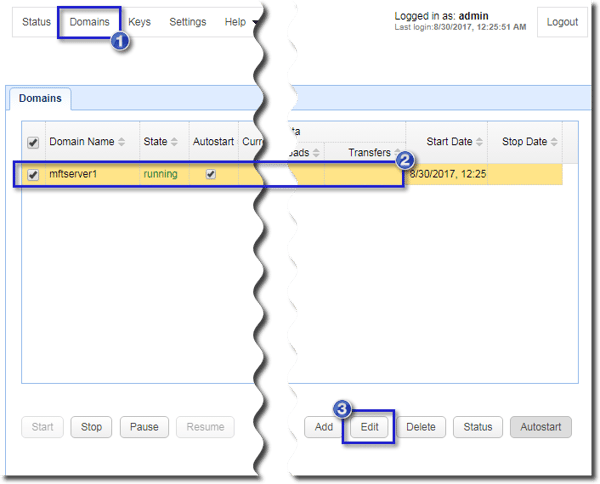
Navigate to the Services module and then click the Add button.
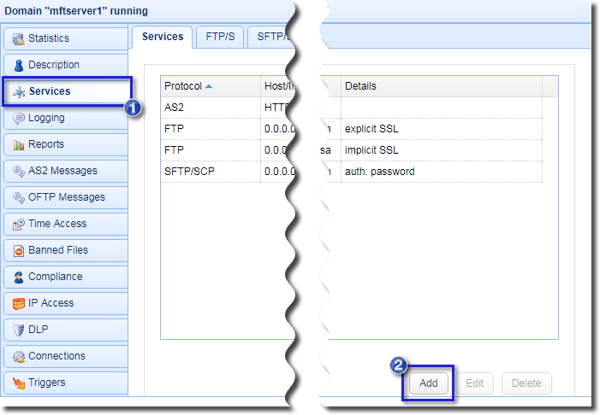
When the pop-up window appears, select HTTP/S from the drop-down list and then click OK.
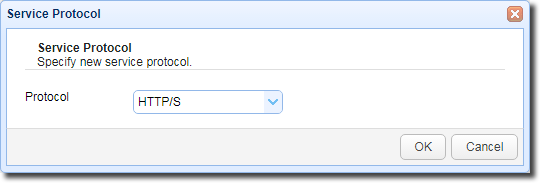
In the next screen, tick the HTTP and HTTPS checkboxes, then click the OK button.
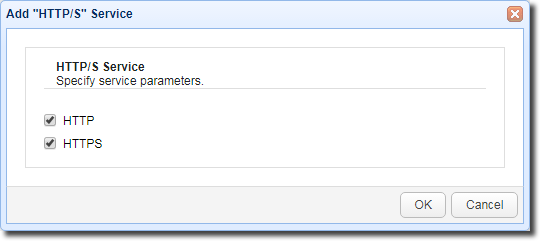
You should then see your newly added HTTP/S service in your list of services.
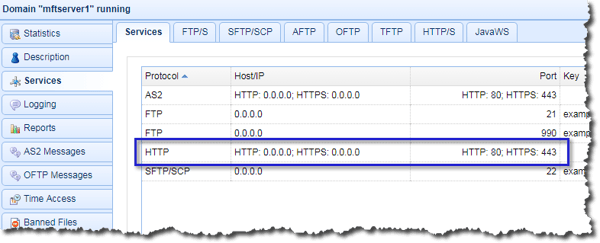
At this point, you would now have an operational HTTPS file transfer service, which you can try using in a test environment. However, be advised that it's unsuitable for a production environment, especially one facing the web.
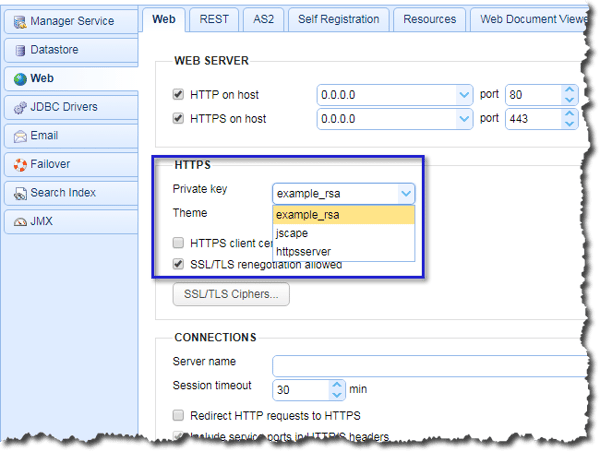
First, the default server key employed is only the example_rsa key that came with your JSCAPE MFT Server installation. You would want to replace that with something representative of your organization and, of course, more secure. Let me now show you where you can do that.
Preparing Server Keys
Before we replace example_rsa, let me explain first what this key is for. This key is known as a Server Key. In the context of the Key Manager, the Server Key actually consists of three elements: a private key, a digital certificate, and a public key. Here's how these three elements come into play.
When a user's Web browser first connects to your server via HTTPS, your server will look up which server key was assigned for the service and then send the corresponding digital certificate and public key back to the browser.
The digital certificate will serve as your server's credentials and help the user's browser determine whether your HTTPS server can be trusted. In order for the browser to trust your server's digital certificate, the certificate should bear a Certificate Authority's (CA's) digital signature. Without that signature, the browser would alert the user like this:
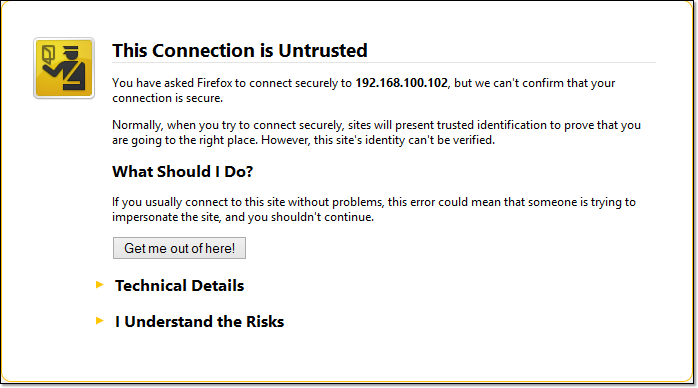
The user can still disregard that warning and proceed to log in to your server, but at least he would have already been notified of the risks.
On the other hand, the public and private keys will be used to secure certain pieces of data that are exchanged during what is known as the SSL Handshake. The SSL handshake is the procedure at the start of an HTTPS file transfer session wherein a web browser and the HTTPS server agree on which set of algorithms (collectively known as cipher suites) should be used during the session.
An SSL handshake culminates with creating a session key, a symmetric key used for encrypting whatever files are uploaded and downloaded during the HTTPS file transfer session.
We'll talk about where you can configure those algorithms in the succeeding section. In the meantime, here's what you must do to prepare a server key.
Go to the Keys menu.
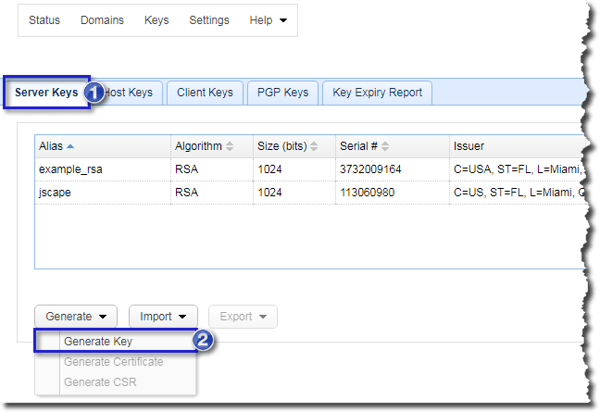
Navigate to the Server Keys tab and then click Generate > Generate Key.
Enter pertinent information, including:
- Key alias - Alias you wish to assign to the key.
- Key algorithm - The algorithm used in generating this key. Valid options are RSA and DSA.
- Key length - The length of the key in bytes. Valid options are 1024 and 2048. Although longer key lengths naturally translate to stronger encryption, they can also be more computationally demanding. Read the article "Choosing Key Lengths for Encrypted File Transfers " for more details on this matter. Note for key lengths greater than 1024, you must install the Unlimited Jurisdiction Policy Files.
- Validity - The number of days this key is valid.
- Common name - The name you wish to assign this key. Typically the domain name this key will serve is ftp.mydomain.com
- Organizational unit - The unit within your organization that this key will be used for, e.g., IT.
- Organization - Your organization name.
- Locality - Your city.
- State/Province - Your state or province.
- Country - Your 2-character country code, e.g., "US".
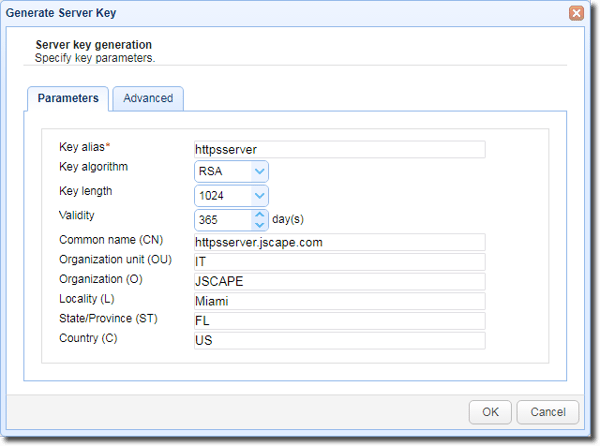
Click OK when done.
You should then see your newly created Server Key.
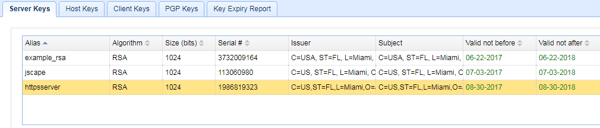
In order for that server key's corresponding certificate to be trusted by your end user's browsers, you would have to submit a Certificate Signing Request (CSR) for this particular server key to a Certificate Authority. This particular process is beyond the scope of this article, but you can find more details in our documentation for Obtaining a trusted certificate.
Once your private key has been signed by the CA, you can then import it. Read the documentation for Importing third-party certificates for details. Pay attention to the "Note" on that page, as some of the problems you may potentially encounter moving forward can be caused by that issue.
After importing, go back to Settings > Web, and then, in the HTTPS panel, select the alias of the newly imported private key. When you're done, click the Apply button at the right corner of that page.
Selecting SSL/TLS Cipher Suites
Earlier, when we briefly touched on a process known as the "SSL Handshake", we mentioned the term "cipher suites". Let me now explain what they're for.
A cipher suite is typically composed of four algorithms:
- An algorithm for key exchanges;
- An algorithm for implementing authentication;
- An algorithm for establishing confidentiality; and
- An algorithm for establishing data integrity
Here's an example of a cipher suite:
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
Here,
- ECDHE, which stands for Elliptic Curve Diffie-Hellman Ephemeral, is the algorithm for exchanging keys;
- ECDSA, which stands for Elliptic Curve Digital Signature Algorithm, is the algorithm for implementing authentication;
- AES_128 is the symmetric encryption key algorithm and is used for establishing confidentiality; and
- SHA256 is the secure hashing algorithm used for establishing data integrity
Before any HTTPS file transfer can occur, your end user's Web browser and your secure Web server must agree on a common set of algorithms. Basically, as soon as the browser first connects via what is known as a "Client Hello", it immediately informs your server which cipher suites it supports. Your server will then check which cipher suites are enabled on its side and choose the most secure.
So, really, if you want maximum compatibility, i.e., you want to make sure your server can serve as many kinds and versions (including legacy) of web browsers as possible, then you need to enable all supported cipher suites on your server.
On the other hand, if you want to achieve maximum security, then you'll have to restrict your HTTPS file transfers to only the most secure cipher suites. A discussion on which cipher suites are the most secure is beyond the scope of this article. But I think it will be a very interesting topic, so stay tuned for that.
To enable or disable SSL/TLS cipher suites, again go back into Settings > Web and click the SSL/TLS ciphers button.
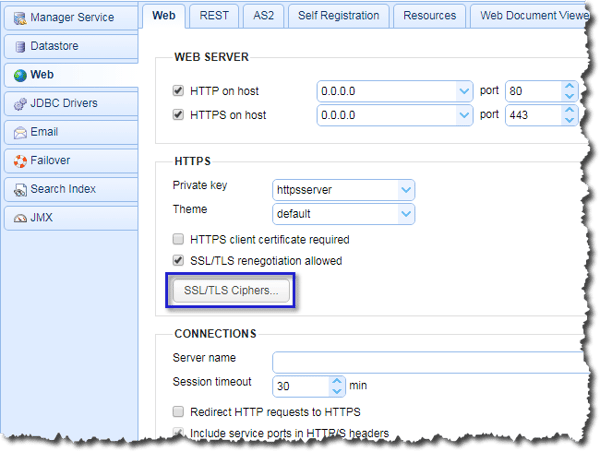
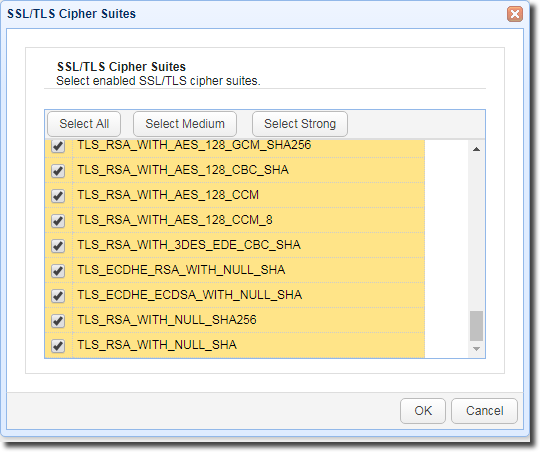
You can then start selecting the SSL/TLS cipher suites you want to enable for your HTTPS file transfers.
Get Your Free Trial
Would you like to try this yourself? JSCAPE MFT Server is platform-agnostic and can be installed on Microsoft Windows, Linux, Mac OS X and Solaris, and can handle any file transfer protocol and multiple protocols from a single server. Additionally, JSCAPE enables you to handle any file type, including batch files and XML. Download your free 7-day trial of JSCAPE MFT Server now.